|
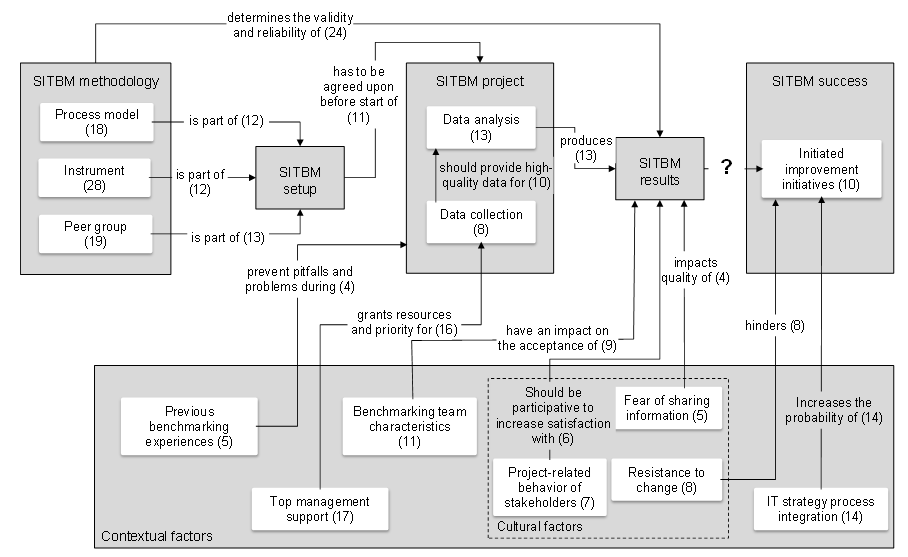
IT organizations use strategic IT benchmarking (SITBM) to revise IT strategies or perform internal marketing. Despite benchmarking’s long tradition, many SITBM initiatives do not reveal the desired outcomes. The vast body of knowledge on benchmarking and IT management does not help overcome the challenges of successful SITBM. In a recently published research project, we therefore synthesize existing research on IT management and benchmarking into a concept relationship map and derive future research avenues. We find that there is much literature on how to produce SITBM results. However, research does not explain how these results are transformed into outcome – essentially the problem many practitioners struggle with. Concept Relationship Map for SITBM Success
Specifically, we found that traditional process models for benchmarking focus on hard methodological factors and tend to neglect the soft contextual ones. We addressed this gap by suggesting a concept relationship map that not only incorporates these hard factors into the benchmarking process, but also provides guidance on the effects of soft aspects. In doing so, we contribute to research and foster comprehensive understanding by synthesizing existing SITBM literature. Moreover, we provide a conceptual model of SITBM success and derive a set of propositions from it. We also shed light on the as-yet-unanswered question of how SITBM output is transformed into outcome. Together with future research weaving together the as yet incomplete nomological net we propose through our proposition, our work can thus lay the foundations for a theory of SITBM success. Our research results have recently been accepted for publication: Ebner, K., Urbach, N. and Müller, B. (2016) Exploring the Path to Success: A Review of the Strategic IT Benchmarking Literature, Information and Management (I&M), forthcoming.
0 Comments
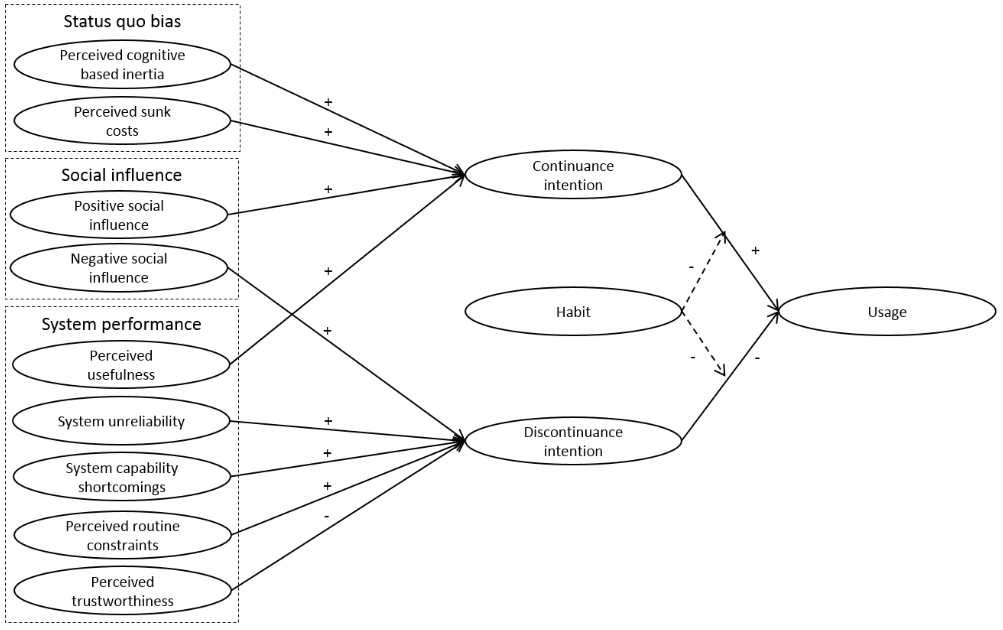
Self-tracking, life-logging, quantified-self, personal analytics, and personal informatics are terms for the current trend to collect and analyze specific features of the life on a regular basis through mobile and wearable digital devices. Users of digital self-tracking devices benefit from information about themselves. Thereby, the explanatory power of this information heavily depends on post-adoption continued usage of these devices. The aim of a recent research project is to empirically analyze the factors that lead to continuous use of self-tracking devices. So far, research has largely focused on phases until IS adoption in a work environment and little on post-adoption use in a consumer context which centers on either continuance or discontinuance. To advance research in this area, we developed a conceptual model that combines both in one comprehensive model by building on established post-adoption theories. Conceptual Model of Self-Tracking Usage
While research on the individual-level continuance/discontinuance of IS is yet scarce, our study is one the first that further explores this promising path and suggests a comprehensive, yet parsimonious model. We will continue our research with a quantitative-empirical evaluation of the developed model. With our research, we aim at contributing to both a better theoretical understanding in the field of IS post-adoption in a consumer context and giving practical implications for producers of self-tracking devices. The research results have recently been accepted for publication: Buchwald, A., Letner, A., Urbach, N. and von Entress-Fürsteneck, M. (2015) Towards Explaining the Use of Self-Tracking Devices: Conceptual Development of a Continuance and Discontinuance Model, Proceedings of the 36th International Conference on Information Systems (ICIS 2015), December, 13-16, Fort Worth, Texas, USA. (Link) In the past, IT organizations were usually coined by the plan-build-run paradigm which structured the activities and processes within the IT organizations with a clear focus on efficiency. Fixed structures in IT allow for efficient work routines and enable automation, but reach their limit in forced innovation work. However, exactly such an innovation work is one of the key characteristics of digitization which leads to new or adapted IT/IS-based business models and value-added activities. In a recent research paper we discuss the limitations of the plan-build-run paradigm and other IT management approaches as well as derive requirements regarding future proof IT organizations. On that basis, we develop the new innovate-design-transform paradigm with which IT organizations can become the innovation drivers within their companies. The research paper will be published soon:
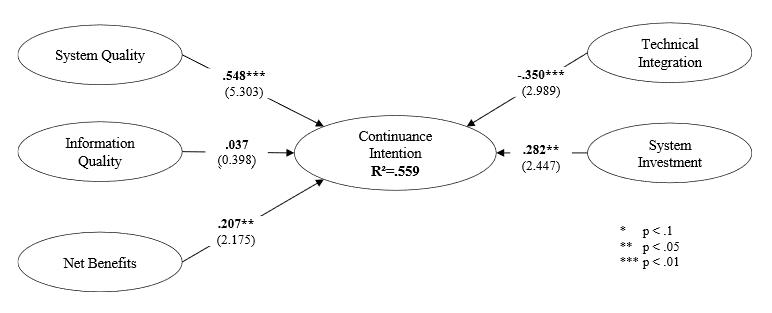
Koch, P., Ahlemann, F. and Urbach, N. (2015) Die innovative IT-Organisation in der digitalen Transformation: Von Plan-Build-Run zu Innovate-Design-Transform, in: Managementorientiertes IT-Controlling und IT-Governance (2. Aufl.), S. Helmke and M. Uebel (eds.). Springer, Berlin: forthcoming. (Link) A growing trend in today’s enterprise applications market is the installation of cloud-based enterprise systems (ES). From consumer goods companies, such as Starbucks, to financial service companies, such as Allianz, more and more companies are implementing cloud-based ES for specific lines of businesses, such as human resource management (e.g. SuccessFactors) or customer relationship management (e.g. Salesforce.com). In addition, there are also a wealth of functionally integrated enterprise resource planning (ERP) service offerings (e.g. SAP Business ByDesign), which now make sophisticated ERP systems affordable to small and medium sized enterprises. As cloud computing has become a mature technology broadly being adopted by companies across all industries, cloud service providers are increasingly turning their attention to retaining their customers. However, only little research has been conducted on investigating the antecedents of service continuance in an organizational context. In a recent research project, we carried out a quantitative-empirical study to address this gap in research. We developed a conceptual model that builds on previous research on organizational level continuance. We tested this model, using survey data gathered from IT decision makers of companies which have adopted cloud enterprise systems. Organizational-Level Drivers of Cloud Continuance
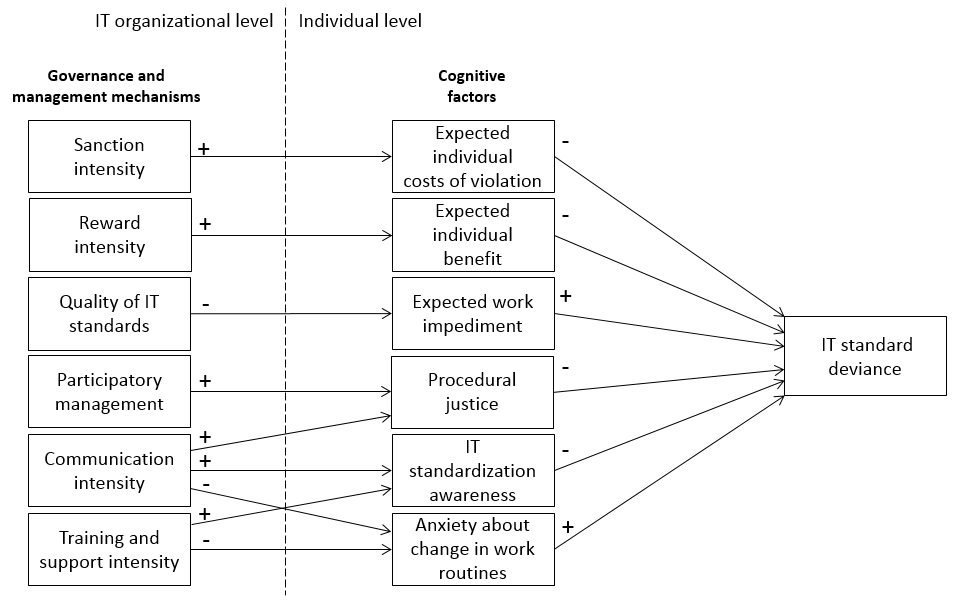
The data was analyzed using PLS. The results show that continuance intention can be predicted both by socio-organizational and technology-related factors. The variables identified were able to explain 55.9% of the variance in continuance intention. System quality had the highest positive effect on the dependent variable, followed by system investment. Information quality showed no significant effect. The research results have recently been accepted for publication: Walther, S., Sarker, S., Urbach, N., Sedera, D., Eymann, T. and Otto, B. (2015): Exploring Organizational Level Continuance of Cloud-Based Enterprise Systems, Proceedings of the 23rd European Conference on Information Systems (ECIS 2015), May 26-29, Münster, Germany. (Link) Organizational information technology (IT) standards have become increasingly important for companies. However, insights from practice indicate that employees tend to violate these standards, generating a need for governance and management mechanisms with which to successfully implement them in the organization. The literature reveals a lack of research on organizational IT standards’ governance. The aim of a recent research project was to idenity the individual and organizational factors that influence an employee’s deviant behavior towards organizational IT standards. We therefore derived a conceptual multi-level model deductively from the literature, which we supplemented with an interview study. Conceptual Model of IT Standard Deviance
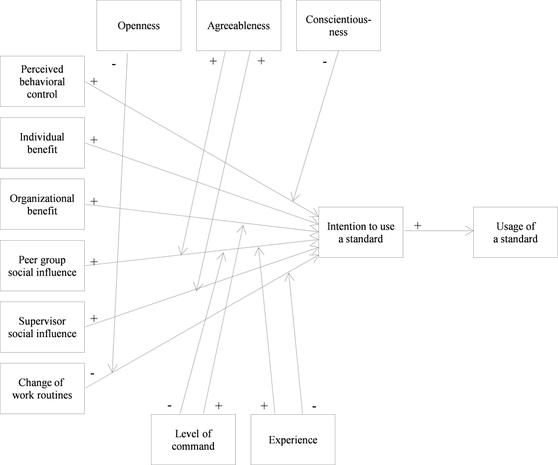
Our work enriches IS research and practitioner bodies of knowledge. We do so by first extending our knowledge of an employee’s deviant behavior towards organizational IT standards. Second, we provide valuable insights for organizations by providing starting points to improve their standardi-zation efforts. The research results have recently been accepted for publication: Dittes, S., Urbach, N., Ahlemann, F., Smolnik S. and Müller, T. (2015) Why don’t you stick to them? – Understanding factors influencing and counter-measures to combat deviant behavior towards organizational IT standards, Proceedings of the 12. Internationale Tagung Wirtschaftsinformatik (WI 2015), March 4-6, Osnabrück, Germany. (Link) Standardizing organizational information technology (IT) infrastructure and processes is stated as one of the most important activities of today’s companies. Since IT is used and embedded in more and more business areas within companies, the complexity and costs of organizational IT infrastructures and processes are continuously rising. In this context, IT standardization represents a possible means to reduce complexity and maintain control over the organizational IT. Given the practical importance of organizational IT standards and standardization efforts, we carried out a database-driven literature search. We found that research on the management, governance and enforcement of IT standards within organizations is relatively limited. Previous studies indicate that many standardization efforts fail suffering from low acceptance rates among staff and rather superficial use Therefore, it is essential for companies to implement management and governance mechanisms to enforce the usage of IT standards in order to achieve their standardization goals. However, before designing such management mechanisms, it is important to first understand the drivers of employee’s acceptance towards organizational IT standards – because without having a deep understanding of employee’s acceptance behavior towards organizational IT standards, it is not possible to design efficient management mechanisms in order to raise the acceptance rate. Therefore it is especially important to understand the cognitive drivers from an employee’s perspective. The aim of a recent research project was to discover the most important influential factors from an employee’s perspective when it comes to accepting or rejecting organizational IT standards by building a perception-based model. Since our work seeks for explaining employee’s acceptance towards organizational IT standards, we embedded our study in the acceptance research stream by deriving a first understanding of the phenomenon. Building on this knowledge, we designed a field study approach based on interviews, resulting in a conceptual model that explains IT standard acceptance on an individual level. Individual Drivers of IT Standard Acceptance
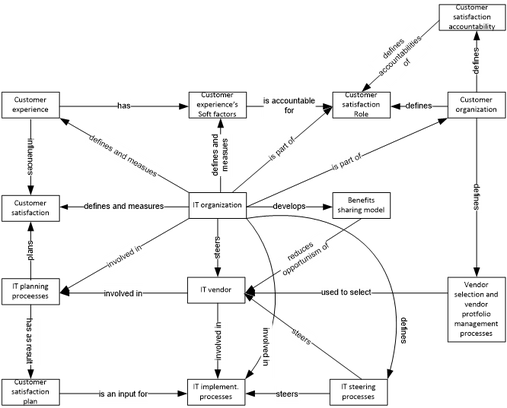
Our work has a twofold contribution: First, we advance the research field on organizational IT standards by establishing links to the field of acceptance research and offering explanations for individual acceptance of those standards. Second, our developed model serves as a basis for managing organizational IT standardization. The research results have recently been accepted for publication: Müller, T., Dittes, S., Ahlemann, F., Urbach, N. and Smolnik, S. (2015) Because Everybody is Different: Towards Understanding the Acceptance of Organizational IT Standards, Proceedings of the 48th Annual Hawaii International Conference on System Sciences (HICSS-48), January 5-8, Kauai, Hawaii. (Link) IT vendor management (ITVM) plays an increasingly relevant role for IT organizations. External vendors play a key role in relation to IT organizations; many companies already spend more than half their IT budgets on products and services from external vendors and are looking to raise the IT budget amount dedicated to external IT procurement. Despite the abundant prescriptive literature on ITVM, studies reveal that companies are often dissatisfied with the deliverables supplied by external IT vendors. The problem of low satisfaction with procured IT products and services is gaining relevance for IT organizations owing to the increased involvement of vendors in the modern IT value chain; increasingly, vendors and their staff are in direct contact with both internal IT personnel and business users. However, despite the importance of a high IT customer satisfaction level for IT organizations, the ITVM literature focuses mainly on enhancing the quality of deliverables and makes no recommendations on how to directly enhance customer satisfaction. To address the problem of dissatisfaction with IT products and services delivered by external vendors, we investigated current ITVM practices and identify improvement areas for these practices in a recent research project. Since there are abundant prescriptions on how to design ITVM in the IS literature, we provide detailed recommendations on how to extend current ITVM practices so as to enhance customer satisfaction. We followed the design science paradigm in information systems (IS) research, which is a problem-solving and prescription-driven paradigm that seeks to create new things that serve human purposes and provide solutions to management problems. Our goal was to extend the ITVM literature by developing a design theory for customer satisfaction-oriented ITVM. Specifically, we aim to (1) derive a generalized set of metarequirements (i.e. generalized requirements) on the ITVM practices to be developed to enhance customer satisfaction, (2) to explain why these metarequirements are met by a generalized set of ITVM design principles (DP) (i.e. generalized design prescriptions), and (3) to deliver blueprints for the implementation of DPs. To answer our research question, we conducted an action research study at a large professional service company. Constructs of the Design Theory
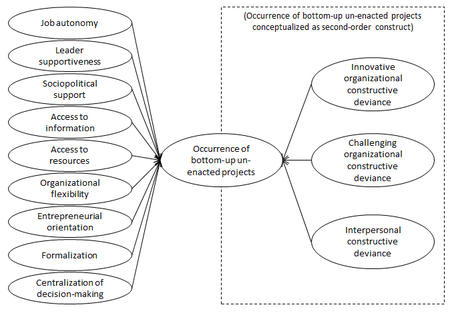
In a recent publication, we theoretically explain and present preliminary empirical evidence of why the implementation of a particular DP is expected to lead to higher customer satisfaction. Our findings indicate that establishing benefits sharing and incentive models for IT vendors, as well as defining and steering customer experience, are the chief management practices that promise improved IT customer satisfaction. Our work’s contribution is twofold: First, we present a generalized design theory for implementing customer satisfaction-oriented ITVM. Second, we develop a basic theoretical understanding of which DPs are needed to enhance customer satisfaction and of how these DPs contribute to reaching this goal. Formulating such DPs can be a first step towards a more general prescriptive research in the field of ITVM, which is dominated by studies on IT outsourcing management and governance. Our research results have immediate practical implications. After having exploited the potential of detailed contracts and strict enforcement of governance guidelines, our research suggests that companies can only reach the next level of ITVM by addressing the “soft” factors that influence customer satisfaction, and by establishing a trustful work atmosphere with IT vendors. In addition, explaining a DP’s MRs is essential for organizations seeking to implement ITVM. This explanation allows companies to better judge whether a certain practice can lead to significant ITVM improvement in a particular organizational setting and to better measure the impact of an ITVM practice. The research results have recently been accepted for publication: Urbach, N., Ahlemann, F. and El Arbi, F. (2014): Towards a Design Theory for Customer Satisfaction-Oriented IT Vendor Management, Proceedings of the 20th Americas Conference on Information Systems (AMCIS 2014), August 7-10, Savannah, Georgia. (Link) Un-enacted projects are those projects that have not been officially evaluated by the project portfolio management but do exist although they are not known to a company’s project portfolio. As a consequence, resources thought to be available often prove to be actually unavailable and that unofficial initiatives eventually compete for scarce resources. One particular type of these un-enacted projects are bottom-up initiatives. Bottom-up un-enacted projects are unofficial initiatives on which employees spend time without order but with which they intend to benefit their organizations. While previous research highlights the great potential of bottom-up un-enacted projects, they only focus on the individual level but leave the organizational level for further research. In a recent research project, we aimed at gaining a deeper understanding of the organizational drivers of bottom-up un-enacted projects. We draw on deviance theory to develop a conceptual model for explaining the occurrence of these projects. In order to triangulate the emerging model with insights from practice, we use interview data to cross-check and refine the theory-driven model. The key result of our work is a conceptual model that comprises the organizational antecedents to explain the occurrence of bottom-up un-enacted projects. Model explaining the occurrence of bottom-up un-enacted projects
Our results advance the theoretical discourse on the concept of un-enacted projects by proposing a conceptual model for explaining the occurrence of a specific type of un-enacted projects, namely bottom-up initiatives, from an organizational perspective. By relying on organizational deviance theory as a theoretical lens, our study is one of the first that applies this reference theory to the field of information systems in general, and more particular to the domain of project portfolio management. From a practical point of view, we expect our model after a thorough empirical evaluation to be a beneficial instrument to evaluate and predict the occurrence of bottom-up initiatives in a particular organizational setting. Having identified the levers for the emergence of such un-enacted projects, responsible practitioners will receive a basis for steering their organization in the intended direction. The research results have recently been accepted for publication: Buchwald, A., Urbach, N. and Ahlemann, F. (2014) Understanding the Organizational Antecedents of Bottom-Up Un-Enacted Projects – Towards a Conceptual Model Based on Deviance Theory, Proceedings of the 22nd European Conference on Information Systems (ECIS 2014), June 9-11, Tel Aviv, Israel. (Link) Theory’s pivotal importance has been continuously emphasized in the information systems (IS) discipline ever since its inception. The ability to understand and contribute to theory is an important qualification in the practice of research. Recently we see some of our reference disciplines turn towards reviving their examination of the concept and how it can help producing high quality scholarly contributions.
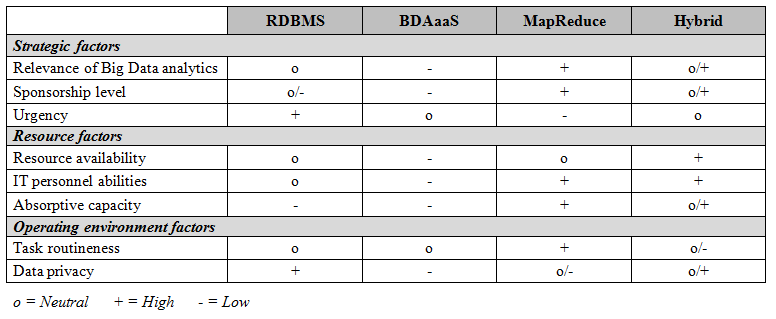
In light of this trend, we suggest that also the IS discipline should intensify its discussion of theory and theorizing. With a recent publication, we thus intend to synthesize and reflect upon the debate on theories and theorizing in the IS field. As such, our key contribution is to inform (new) authors about opportunities in theorizing and help them put the concept of theory to work for them. Through this, we hope to advance and support the discipline’s current strive towards more theoretical thinking and the increasing demand for theoretical contributions. The research results have recently been accepted for publication: Müller, B. and Urbach, N. (2013) The Why, What and How of Theories in Information Systems Research, Proceedings of the 34th International Conference on Information Systems (ICIS 2013), December 15-18, Milano, Italy. (Link) By intelligently using the information in and around them, organizations are able to improve their decision-making and better realize their objectives. Some authors even claim that organizations may lose competitiveness by not systematically analyzing the available information. However, to obtain the desired insights, data need to be sourced, stored, and analyzed. During the past years, accessing and processing the collected, voluminous, and heterogeneous amounts of data has become increasingly time consuming and complex. With a total of 1.8 zettabyte in 2011, the amount of generated data has not yet reached its climax: as expected by IDC, a global provider of IT market intelligence, the total amount of data collected until the end of 2012 is estimated to be 1.48 times the amount of data collected in previous years, with more than 90% of this data being unstructured. Businesses increasingly use these data masses provided by millions of networked sensors in mobile phones, cashier systems, automobiles, or weather stations to learn more about their customers, suppliers, and operations. This development raises the question of how companies manage to cope with the characteristics of the ever-increasing amount of data, referred to as Big Data. In a recent research project we aimed at providing a set of organizational contingency factors that influence different Big Data strategies organizations may implement. In order to do so, we reviewed existing literature to identify different Big Data strategies as well as contingency factors and synthesized both into a contingency matrix that may support practitioners in choosing a suitable Big Data strategy for their specific context. Impact of identified contingency factors on Big Data strategy choice Based on our analysis, we found that different organizational environments pursue different requirements on a Big Data strategy. To better support practitioners in Big Data strategy choice, we compared the four identified Big Data strategies regarding how well they addressed each of the contingency factors. For instance, when the relevance of Big Data analytics is high in a company, the MapReduce strategy seems most fruitful (resulting in a “+” assessment). However, also a hybrid solution might be valuable in case it follows a MapReduce-dominant approach. If in turn an RDBMS-dominant implementation is chosen, the hybrid strategy is only slightly better than a “pure” RDBMS approach (resulting in a “+/o” assessment).
The research results have recently been accepted for publication: Ebner, K., Bühnen, T. and Urbach, N. (2014) Think Big with Big Data: Identifying Suitable Big Data Strategies in Corporate Environments, Proceedings of the 47th Hawaii International Conference on Systems Sciences (HICSS-47), January 6-9, Hilton Waikoloa, Big Island. (Link) |
Archives
December 2015
Categories
All
|

 RSS Feed
RSS Feed
